Overview of TLS 1.3
TLS 1.3 (Transport Layer Security version 1.3) is a cryptographic protocol that secures communication between two parties—typically a client (e.g., a web browser) and a server (e.g., a website). Standardized in August 2018 by the IETF (RFC 8446), it encrypts data, verifies identities, and ensures integrity. It’s designed for speed and security, improving on TLS 1.2 by simplifying processes and eliminating vulnerabilities.
TLS 1.3 operates at the transport layer of the OSI model, sitting between the application layer (e.g., HTTP) and the network layer (e.g., TCP/IP). It’s widely used for HTTPS, email (SMTP, IMAP), VPNs, and more.
How TLS 1.3 Works: The Handshake Process
The core of TLS 1.3 is its handshake, which establishes a secure connection. Unlike TLS 1.2’s two-round-trip (2-RTT) handshake, TLS 1.3 streamlines it to one round-trip (1-RTT), reducing latency while enhancing security. Here’s how it unfolds:
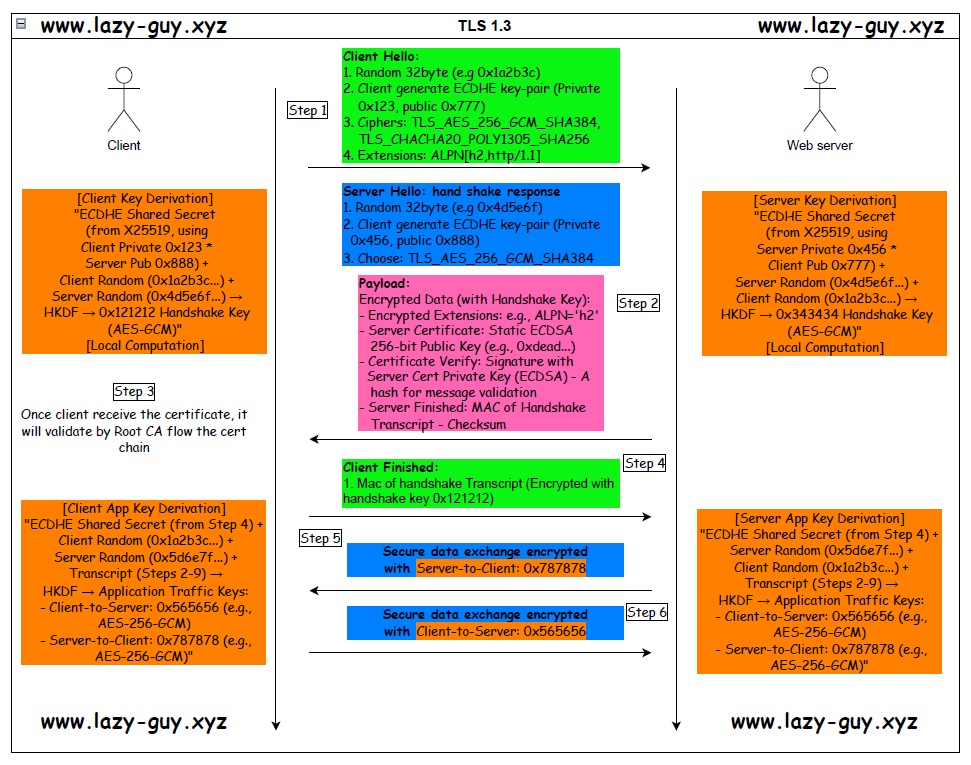
1. ClientHello (Client Initiates)
- What Happens: The client (e.g., your browser) sends a “ClientHello” message to the server.
- Contents:
- TLS Version: Specifies TLS 1.3 (or a fallback like 1.2 for compatibility).
- Cipher Suites: A list of supported cryptographic algorithms (e.g., TLS_AES_256_GCM_SHA384, TLS_CHACHA20_POLY1305_SHA256). These define encryption (AES or ChaCha20) and integrity (SHA-256 or SHA-384).
- Key Share: A public key share for Diffie-Hellman (DH) key exchange, typically using elliptic curve groups (e.g., X25519). This is sent upfront to speed things up.
- Extensions: Additional data like “Supported Groups” (DH parameters), “Server Name Indication” (SNI for virtual hosting), and optionally “Pre-Shared Key” (PSK) for session resumption.
- Purpose: Offers the server everything it needs to pick a secure configuration and start the key exchange.
2. ServerHello (Server Responds)
- What Happens: The server replies with a “ServerHello” message.
- Contents:
- Selected Cipher Suite: Picks one from the client’s list (e.g., TLS_AES_256_GCM_SHA384).
- Key Share: The server’s public key share for Diffie-Hellman.
- Certificate: A digitally signed certificate (usually X.509) proving the server’s identity, issued by a trusted Certificate Authority (CA).
- Signature: A digital signature over the handshake messages, using the server’s private key, to verify authenticity.
- Encryption Begins: After sending its key share, the server encrypts the rest of its response (certificate, signature) using keys derived from the shared secret. This hides metadata that was plaintext in TLS 1.2.
- Purpose: Confirms the connection parameters and proves the server’s legitimacy.
3. Key Derivation
- What Happens: Both client and server compute a shared secret using the Diffie-Hellman key exchange.
- The client combines its private key with the server’s public key share.
- The server does the same with its private key and the client’s public key share.
- Result: A shared secret (unique to this session) that no eavesdropper can derive, thanks to DH’s mathematical properties.
- Session Keys: Multiple keys are derived from this secret using a key derivation function (HKDF with SHA-256 or SHA-384):
- Traffic Encryption Keys: For symmetric encryption (e.g., AES-256-GCM).
- Integrity Keys: For message authentication codes (MACs).
- Handshake Keys: For encrypting the handshake itself.
- Forward Secrecy: Since the shared secret is ephemeral (discarded after the session), compromising a long-term key (e.g., the server’s private key) doesn’t decrypt past sessions.
4. Finished Messages
- What Happens: Both parties send a “Finished” message.
- Contents: A hash of all handshake messages, encrypted with the session keys, proving no tampering occurred.
- Purpose: Verifies the handshake’s integrity and confirms both sides have the same keys.
5. Data Transmission
- What Happens: With the handshake complete (in 1-RTT), the client and server begin exchanging application data (e.g., web pages).
- Encryption: Data is encrypted with the symmetric cipher (e.g., AES-GCM) and tagged with a MAC for integrity.
- Record Protocol: TLS 1.3 wraps data in “records” (small packets) with headers indicating content type (e.g., handshake, application data).
Optional: 0-RTT Resumption
- How It Works: For repeat connections (e.g., revisiting a site), TLS 1.3 offers “zero round-trip time” (0-RTT) resumption.
- Mechanism:
- In a prior session, the server sends a “Pre-Shared Key” (PSK) to the client.
- On reconnection, the client sends encrypted data alongside the “ClientHello” using the PSK, skipping the full handshake.
- Trade-Off: Faster (no round-trips), but vulnerable to replay attacks (an attacker resending captured data). Used cautiously (e.g., for idempotent requests like GET).
Security Features of TLS 1.3
- Stronger Cipher Suites:
- Only supports authenticated encryption with associated data (AEAD) modes like AES-GCM and ChaCha20-Poly1305. These combine encryption and integrity in one step.
- Drops weak ciphers (e.g., RC4, CBC modes) prone to attacks like BEAST or Lucky Thirteen.
- Forward Secrecy Mandatory:
- Eliminates RSA key exchange (where the session key was encrypted with the server’s public key, risking past decryption if the private key leaked).
- Uses ephemeral Diffie-Hellman exclusively.
- Encrypted Handshake:
- Post-“ServerHello,” nearly all handshake messages are encrypted, hiding certificate details and extensions from passive observers.
- Removed Vulnerabilities:
- No compression (avoids CRIME attack).
- No renegotiation (prevents man-in-the-middle exploits).
- Drops MD5, SHA-1, and DES (broken or weak algorithms).
- Simplified Design:
- Fewer options reduce misconfiguration risks and attack surfaces.
Why It’s Secure and Fast
- Speed: The 1-RTT handshake cuts connection time in half compared to TLS 1.2’s 2-RTT. 0-RTT boosts repeat visits.
- Security: Encrypted handshakes, forward secrecy, and modern ciphers thwart eavesdropping, tampering, and retroactive decryption.
- Practical Example: When you visit an HTTPS site in 2025, TLS 1.3 ensures your login credentials and data stay private, even on public Wi-Fi.