As a WordPress blogger running www.lazy-guy.xyz, I’ve always been curious about my site’s security. With cyber threats lurking around every corner, I decided to take action and scan my blog using WPScan, a powerful tool designed to uncover vulnerabilities in WordPress sites. What I found—and fixed—might surprise you! In this post, I’ll walk you through my journey, from scanning my blog to locking it down, so you can secure your own WordPress site too.
Step 1: Scanning My Blog with WPScan
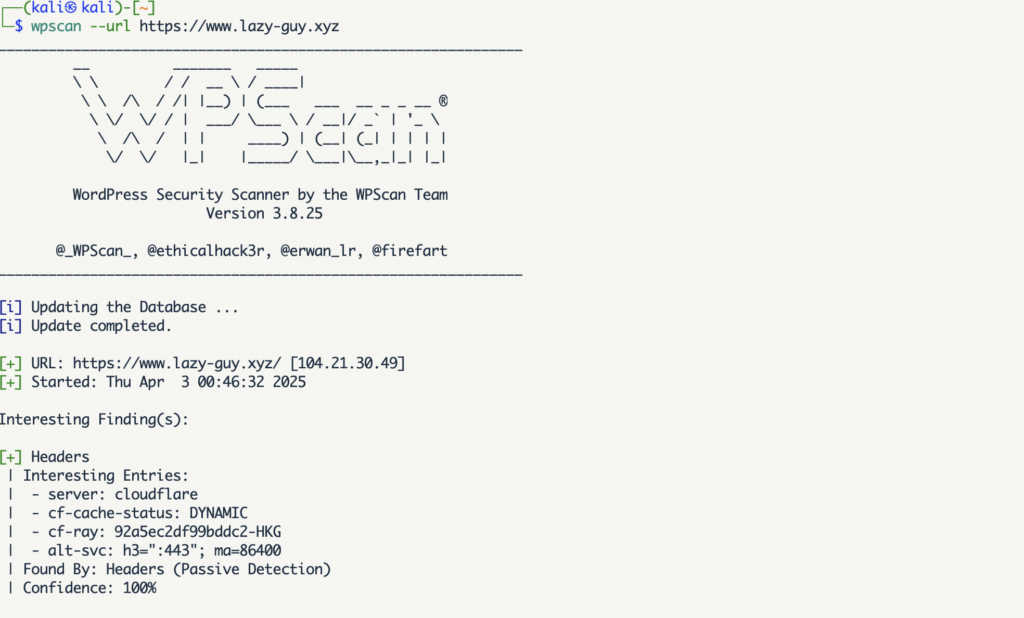
I fired up WPScan, a free command-line tool built for WordPress security audits, to analyze www.lazy-guy.xyz. It’s pre-installed on Kali Linux (a hacker-friendly OS I use for testing), and after a quick wpscan –update, I ran this command:
wpscan --url https://www.lazy-guy.xyzThe scan took about 45 seconds and revealed some eye-opening details about my site. It checked my WordPress version, theme, plugins, and potential weak spots. Here’s what stood out:
- Readme File Exposed: A readme.html file was sitting in my site’s root, potentially leaking my WordPress version.
- Uploads Directory Listing: My /wp-content/uploads/ folder was wide open, showing a list of files to anyone who visited.
- WP-Cron Accessible: The wp-cron.php file could be hit externally, risking a Denial of Service (DoS) attack.
- Plugins and Theme: I’m using the Astra theme and plugins like Yoast SEO, all mostly up to date—except Yoast, which needed a nudge to the latest version.
No critical vulnerabilities popped up, but these findings were enough to get me moving. Time to secure my blog!
Step 2: Fixing the Issues
Armed with WPScan’s report, I rolled up my sleeves and made some changes. Here’s how I tackled each problem, step-by-step.
Locking Down the Uploads Directory with Options -Indexes
The /wp-content/uploads/ folder showing its contents was a big no-no. This “directory listing” could let attackers see my uploaded files—think images, PDFs, or even accidental backups. To fix it, I added a line to my .htaccess file in my WordPress root directory:
Options -IndexesWhat does Options -Indexes do? It tells Apache (my web server) to stop displaying file lists. Before, visiting https://www.lazy-guy.xyz/wp-content/uploads/ showed everything inside. After adding this, it returns a “403 Forbidden” error—exactly what I wanted. My media files are still accessible via direct links (like in blog posts), but no one can browse the folder. I tested it in my browser, and boom—403 confirmed!
Removing the Readme File
That readme.html file? It’s a default WordPress file that often reveals your version number—a breadcrumb for hackers. I decided to delete it outright:
rm readme.htmlI checked https://www.lazy-guy.xyz/readme.html afterward, and it returned a 404 Not Found—gone for good! WordPress might recreate it on updates, so I could also block it in .htaccess with:
RedirectMatch 403 readme\.html$For now, deletion worked fine.
Securing WP-Cron
WPScan flagged wp-cron.php as externally accessible. This file runs scheduled tasks (like publishing posts), but if attackers spam it, it could slow my site down. I added this to .htaccess to block outside access:
<Files "wp-cron.php">
Order Deny,Allow
Deny from all
Allow from 127.0.0.1
</Files>Now, only my server can trigger it. For extra control, I could disable WP-Cron in wp-config.php and set up a server cron job, but this fix was quick and effective.
Updating Yoast SEO
My Yoast SEO plugin was at version 24.7, while 24.8 was the latest. Outdated plugins are a common entry point for exploits, so I logged into my WordPress dashboard, hit Plugins > Updates, and bumped it up. Easy peasy!
Step 3: Hardening Other Paths
With the main issues fixed, I looked at other files in my WordPress root. Here’s what I did:
- Blocked xmlrpc.php: This legacy API file is a known target for attacks. I added:
<Files "xmlrpc.php"> Order Deny,Allow Deny from all </Files> - Protected wp-config.php: My config file holds sensitive data like database credentials. It wasn’t exposed, but I added a safeguard:
<Files "wp-config.php"> Order Deny,Allow Deny from all </Files> - Cleaned Up: I deleted license.txt and wp-config-sample.php—unnecessary files that could hint at my setup.
My final .htaccess looks like this:
# BEGIN WordPress
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteRule .* - [E=HTTP_AUTHORIZATION:%{HTTP:Authorization}]
RewriteBase /
RewriteRule ^index\.php$ - [L]
RewriteCond %{REQUEST_FILENAME} !-f
RewriteCond %{REQUEST_FILENAME} !-d
RewriteRule . /index.php [L]
</IfModule>
# END WordPress
Options -Indexes
RedirectMatch 403 readme\.html$
<Files "wp-cron.php">
Order Deny,Allow
Deny from all
Allow from 127.0.0.1
</Files>
<Files "xmlrpc.php">
Order Deny,Allow
Deny from all
</Files>
<Files "wp-config.php">
Order Deny,Allow
Deny from all
</Files>Step 4: Verifying the Fixes
I re-ran WPScan with an API token (get one free at wpscan.com) to double-check:
wpscan --url https://www.lazy-guy.xyz --enumerate vp --enumerate vt --api-token YOUR_TOKENThe uploads listing was gone, readme.html was history, and no new red flags appeared. My admin console (/wp-admin/) worked perfectly—Options -Indexes didn’t break a thing, as WordPress doesn’t rely on directory browsing.
Why This Matters for WordPress Security
Running WPScan on www.lazy-guy.xyz showed me how small oversights—like an exposed uploads folder or an old plugin—can invite trouble. WordPress powers over 40% of the web, making it a juicy target. Simple fixes like these reduce your attack surface without needing a tech degree. Plus, with Cloudflare already on my site, I’ve got an extra shield against threats.
Takeaways for Your Site
Want to secure your WordPress blog? Here’s my advice:
- Scan with WPScan: It’s free and reveals hidden risks.
- Fix Directory Listing: Add Options -Indexes to your .htaccess.
- Remove Junk Files: Ditch readme.html, license.txt, etc.
- Lock Down Key Files: Block xmlrpc.php, wp-cron.php, and wp-config.php.
- Stay Updated: Keep your theme, plugins, and WordPress core current.
Got questions? Drop a comment below—I’d love to hear how you secure your site! For now, www.lazy-guy.xyz is tougher than ever, and I’m sleeping better knowing it’s locked down.